In this Article
When configuring a proxy server in DataImpulse, you can stumble upon an option to exclude an autonomous system number. What is an autonomous system number, and why do you need to exclude it? How might excluding it benefit your business, and when is it not the best option? Read below.
What is an autonomous system number, and why do you need it?
An autonomous system (AS) is a huge group of networks managed by a single organisation, like an internet service provider. Each AS has its number called the Autonomous System Number (ASN). You can think of it as a name. Networks that make up an AS share a common routing policy — a set of rules about how to transfer the data.
Autonomous networks are necessary to put the global web in order. A lot of people use the Internet simultaneously to transfer or retrieve huge volumes of data, so it’s essential to establish clear paths for that data. Otherwise, the web would become a complete mess.
To understand the concept of autonomous networks, imagine that you travel from Tokyo to New York. There is no direct flight, so you need to take several. There are a few options. For example, you can go to Berlin and then to New York. Or you can go to Seoul, then to Mexico, and then to New York. The first option is obviously better because it’s a much shorter distance. Data travels globally in just the same manner: choosing the shortest way, going from one point to another, until it reaches the final destination. In this analogy, cities are like autonomous networks — huge independent systems that serve as intermediaries and final points.
There are a lot of autonomous systems across the web. Some of them are bigger, and some are smaller. Every AS has a set of IPs that belong to it. Such sets are called “IP address spaces.” IPs that belong to the same AS have the same prefix — a number written after a slash. For example, in an address 111.222.3.44/5, “5” is the prefix.
When you configure a proxy server, you can exclude a particular AS. It means that your data won’t be proxied via the IPs of that AS. For it, you only need to enter an ASN in a corresponding field.
Why exclude certain autonomous systems, and how may it benefit your business?
- Improved performance
Some autonomous systems may have a suboptimal route; in that case, data travels longer than it should. Alternatively, the hardware utilised by servers of an AS may be out-of-date. Or there are other technical limitations, like the number of servers used by an AS. Worst of all, there are autonomous systems with low bandwidth capacity that can’t support traffic-consuming tasks like web scraping. As a result, you experience high latency or poor overall performance. By excluding those ASNs, you can avoid such difficulties and have a stable, fast connection. For example, you can route your data via autonomous systems with servers closer to your proxy and exclude other systems. It will help you lower latency.
- Enhanced security
Not only individual IPs but the entire autonomous systems are often associated with harmful activities such as hosting attacks, spreading malware, spyware, and spam. If you route your traffic in such a way, you may expose your sensitive information to bad actors or infect your devices with a virus. You may be associated with those IPs, which won’t be good for your reputation. Moreover, such IPs may be blocked by a lot of sources. So, using them, you won’t be able to reach the websites you need. Because of this, you may want to exclude certain ASNs. Your traffic won’t go through that particular AS, keeping you and viruses and possible reputation damage away from each other.
- Compatibility
There may be situations when your proxy server isn’t compatible with certain autonomous systems due to different routing policies. In other words, a proxy server transfers information according to certain rules, and an AS’s servers do it according to other rules. Or a proxy’s software or hardware is much more up-to-date or out-of-date compared to an AS’s. If those rules or software aren’t compatible, you may face difficulties if you try to route your traffic through the IPs of that AS. For example, you may experience constant errors or security issues. It’s better to exclude such autonomous systems beforehand because if you try to use them, you’ll be left with no results.
Your intention to exclude certain ASNs may be about business as well. For example, your company might have a peering agreement with certain autonomous systems. That’s why you might want to exclude other ones.
Downsides of excluding autonomous systems
When excluding autonomous systems, you have to remember that this decision might also have negative consequences depending on traffic patterns, network topology, and other factors.
- Reduced options
Excluding certain autonomous systems from a list may leave you with few options to choose from. There will be fewer paths available for your data. If something happens to an AS you use, a proxy server won’t have any alternative ways to route your traffic. It may result in high latency, errors, or even leave you with no connection at all.
- Limited access
Some websites may be hosted within blocked autonomous systems. You won’t be able to visit them and view the content. If you try to, for example, scrape a number of websites and collect data, you may end up empty-handed if you exclude too many autonomous systems.
- Unreliable blocking
If you mean to block a range of IPs by blocking an AS they belong to, you should know that it isn’t the best way. IPs may be reassigned over time. This way, the source that you want to block may become accessible because it has a new IP. One more reason: an AS that IPs are associated with may change. So, AS-level blocking alone isn’t a 100% guarantee that you will restrict all unwanted sources. On top of that, a lot of IPs belong to a single AS. If you block the whole AS because of one or two IPs, it may be unreasonable.
- Complex maintenance
You need to always monitor the list of excluded autonomous systems. They can merge with other systems. Their performance may vary. So, you should keep an eye on the list of blocked systems. Not in every case this is worth the time and money that this requires.
With all of this, you should weigh the pros and cons and exclude autonomous systems only if the real need exists. Sometimes you may have to consult with several IT specialists to understand whether excluding autonomous systems is a good way for you.
How do you identify AS with issues?
How do you know what AS to exclude and what to trust? There are several ways and tools to check an AS and decide whether to use it or avoid it.
- Network monitoring tools
There are numerous instruments, such as Ookla Speedtest, Wireshark, or PingPlotter, designed to help control how networks perform. Those include network monitoring platforms, traceroute, and pings. Such tools can help you with tracking the network path, measuring latency, and detecting packet loss. Using them, you can nail down autonomous systems with operation or connectivity problems.
- Looking Glass servers
Many internet service providers offer Looking Glass servers. Such servers are necessary to conduct network diagnostics and identify autonomous systems with issues. In contrast to network monitoring tools, Looking Glass servers provide you with more detailed information, including routing tables and network statistics. With such servers, you can also perform connectivity testing. For this, you have to input the IP address or hostname of a source, and the Looking Glass server then sends echo request packets. Then the server unveils the echo reply packets received, confirming the reachability of the target server from a current network. If you want to use Looking Glass servers, Telia Carrier Looking Glass or Hurricane Electric Looking Glass are options worth considering.
- Public internet outage maps, peeringDB, forums, mailing lists
Public internet outage maps, such as Cloudflare Status or ThousandEyes, are services or platforms that contain real-time or near-real-time data about known network issues, for example, network anomalies or connectivity problems. There are several sources that such maps get data from, including network monitoring data and user reports.
PeeringDB is an online database that collects information about network interconnections and peering agreements between autonomous systems. PeeringDB is community-driven: network organisations such as internet service providers and organisations with peering relationships keep the information up-to-date, providing valuable insights into how different systems perform. There are a lot of companies with profiles on peeringDB, including Google, Netflix, and Facebook.
Forums and mailing lists are also great sources of information. Here, users share their insights about different aspects related to autonomous systems, and you can find valuable information. PeeringDB mailing list, NANOG, Cisco Support Community, and Network Engineering Stack Exchange are prominent examples of such communities.
- Threat intelligence platforms and IP reputation databases
To identify autonomous systems with security issues, such as spreading viruses, malware, spyware, or hosting attacks, you can use various instruments.
Threat intelligence platforms are databases and systems that collect, store, and disseminate information about security threats. They use open-source intelligence, dark web monitoring, commercial feeds, and honeypots as sources of data. The most well-known examples include FireEye Threat Intelligence, IBM X-Force Exchange, and Recorded Future.
IP reputation databases, also called IP blacklists or IP reputation services, are databases that store information about IP addresses based on their behaviour. Using those databases, you can check whether an IP is associated with any illegal activities, like spreading viruses or hosting attacks. Spamhaus, Cisco Talos Intelligence, and Fortinet FortiGuard IP Reputation are among the most informative ones.
How to exclude ASNs with DataImpulse?
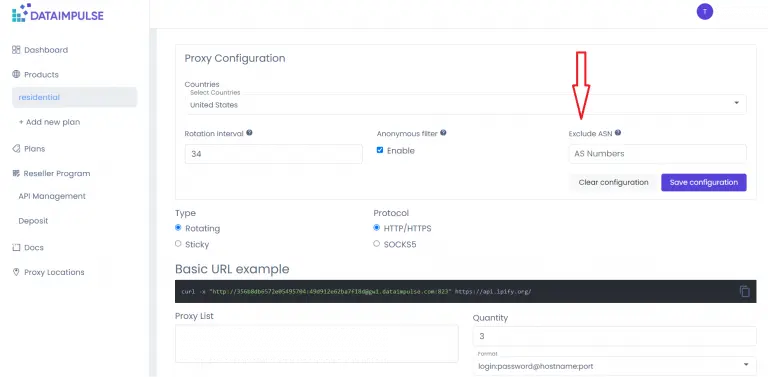
DataImpulse offers you the feature of excluding autonomous systems. To do this, you should log in to your account and go to the “residential” tab.
Here, find the “Proxy Configuration” section. On the right, you’ll see the “Exclude ASN” feature.
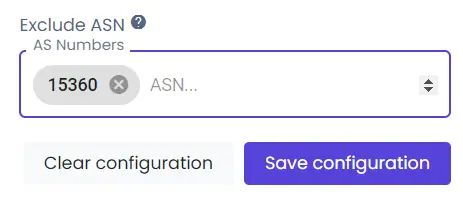
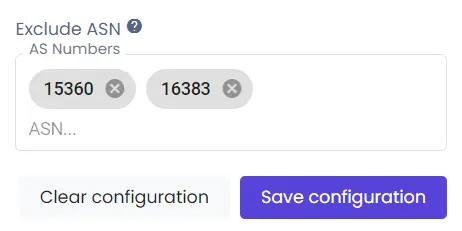
Then you need to enter a number or numbers of ASNs you don’t want to route traffic through. You can exclude one or several ASNs.
You can enter and edit ASNs manually or use counters. To confirm the settings, click on the “Save configuration” button. If you change your mind, use the “Clear configuration” button, and you’ll delete all the current settings. You can also delete numbers one by one.
If you need any help, our support team is available 24/7, even on weekends and holidays. You can contact us by clicking on a widget in the bottom right corner of the screen.
To wrap up
Whether to exclude particular ASNs from your proxy list or not is a serious question. There is no definite answer; everything depends on a lot of factors, including performance, maintenance, security, and compatibility of autonomous systems. Special tools, databases, and platforms will help you know more about autonomous systems and make the right decision. DataImpulse, in turn, provides you with a user-friendly dashboard to exclude ASNs and set up your proxy server in a matter of minutes. Our support team is at your service 24/7. With us, you pay only for the traffic you consume. Click on the “Try now” button or contact us at [email protected] to start.