In this Article
Once you get closer to how the web really works, you discover that nothing happens randomly. Modern web communication runs on protocols—rules that define how data is sent and received. Many users think the internet just feeds you all the data instantly when you open a site, but the actual process is far more structured.
Here, we’ll take a look at TCP and UDP, what they are, and why understanding them is important if you work with proxies.
I am raw html block.
Click edit button to change this html
Why Your Proxy Workflow Depends on TCP and UDP
After reading this article, you already know how the Internet serves you. The data delivery depends on the transport layer of the network stack. TCP and UDP operate exactly there, and any proxy traffic must follow one of these paths. They affect everything: how long your connection stays open, how packets are handled under load, how proxies relay your traffic through their infrastructure, and how services interpret incoming requests.
These are the core transport methods, and they influence everything from latency to packet integrity inside a proxy system.
Uncovering TCP
TCP stands for Transmission Control Protocol. This protocol gives us specific guarantees about how the transfer of bytes happens. It is basically one of the main protocols the internet is built upon. TCP is so popular because it is very reliable.
The byte stream you send is split into packets, and each packet gets additional information. This information can include the port you’re sending the message to, the size of the message, a checksum, and a sequence number. Then we send this packet to the recipient. The recipient receives it and begins to verify it. For example, it calculates its own checksum and compares it with the one encoded in the packet. If they match, it means the packet arrived intact. In this case, the receiving side sends back a confirmation like: “I received the packet with this sequence number; please send the next one.”
On the sender’s side, once we get this confirmation, we send the next packet. But sometimes a packet may simply get lost on the way. In that case, the recipient again calculates the checksum, compares it to the one in the packet, sees that they differ, and sends a response like: “Please resend the packet with this sequence number.”
The sender then resends that packet, and this process is repeated until the packet arrives correctly, and we get a confirmation. This protocol is made for the reliable transmission of a data stream. The price we pay for this reliability can be speed because if a part of the message is lost, we must resend it, which slows down communication.
What is UDP?
UDP stands for User Datagram Protocol. It is much simpler than TCP, but this protocol does not provide any reliability guarantees. Instead, its main advantage is speed.
One of the key differences is that UDP works with individual messages (datagrams). Each message has a fixed length, and we send it as a whole without splitting it into packets, without confirming anything, essentially without doing any additional work.
We have no guarantees that the message will reach the recipient at all. We can send a message, it may get lost somewhere on the way, and that’s it. The recipient won’t even know that something was sent. Or the message may arrive damaged.
UDP is useful when reliability isn’t critical. It’s ideal for real-time audio or video, supporting broadcast or multicast to quickly reach many devices, which is handy for chats, multiplayer games, or streaming. UDP is fast because it does no confirmations, no retransmissions, and has no reliability mechanisms.
TCP vs UDP
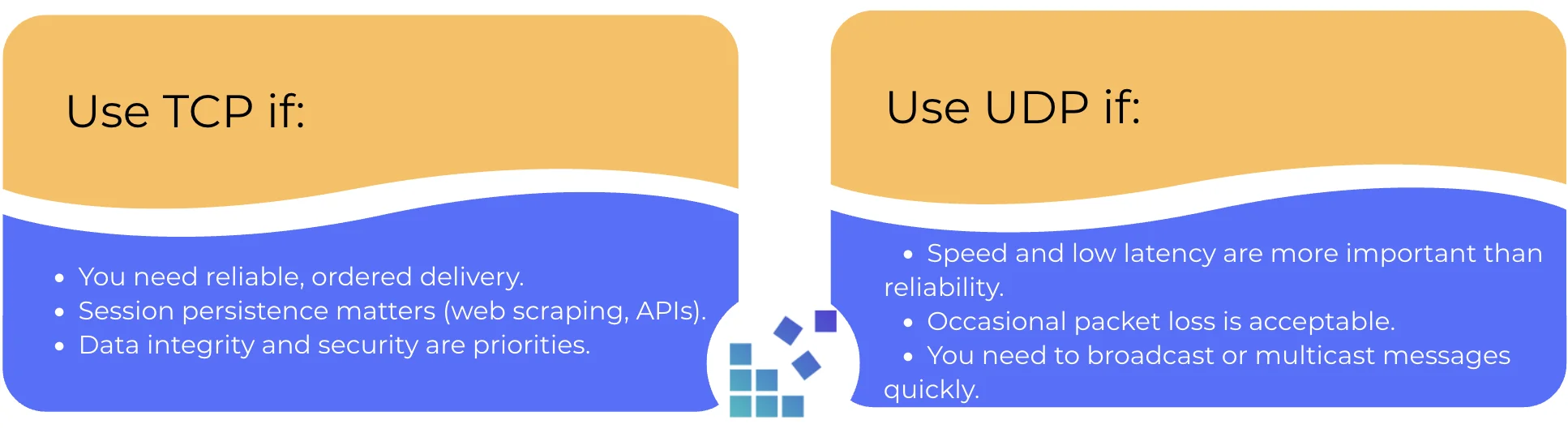
TCP and UDP define how data is transferred over the network, but they do it in very different ways. TCP sends data reliably, in order, and in parts, making sure every byte reaches its destination. We need TCP for activities that require consistency and accuracy, for example, web automation, online transactions, file transfers, etc.
UDP, on the other hand, is faster and lighter because it doesn’t ensure delivery or ordering. It’s suitable for real-time applications like video or audio streaming, multiplayer games, and IoT devices, where some packet loss is acceptable and speed is more important than perfect reliability.
What about the security aspect?
TCP is connection-oriented. However, its handshake mechanism can be exploited in SYN flood attacks, where hackers overwhelm servers with incomplete connection requests. TCP connections can also be disrupted using forged RST (reset) packets or sequence number prediction attacks. UDP is connectionless. It’s vulnerable to IP spoofing, reflection, and amplification attacks. Because of this, many proxy providers restrict or rate-limit UDP traffic to reduce potential abuse.
| Characteristic | TCP | UDP |
| Type of transmission | Connection-oriented | Connectionless |
| Reliability | High | Low |
| Speed | Slow | Fast |
| Proxy suitability | Stable connections | Useful for low-latency traffic |
| DoS risks | Vulnerable to SYN floods | Vulnerable to UDP floods |
| Spoofing | Harder but possible | Easier due to the lack of handshake |
How Proxies Handle TCP and UDP Traffic
Most residential and mobile proxies support both protocols, but TCP is generally preferred because its reliable design works well for session-based tasks like web scraping or API calls. UDP support exists but is often limited through rate-limiting or filtered ports. Proxies also handle NAT and packet translation in order to guarantee proper request and answer flow between client devices and target servers.
TCP connections are easier to trace and monitor, while UDP offers faster transmission and some level of anonymity, but may be restricted on proxy networks, which can impact latency-sensitive traffic.